10 Best Network Security Policy Management Tools | NSPM Software
Are you looking for the Best Network Security Policy Management Tools (NSPM Tools)?
One of the main issues that preoccupied enterprises is how to manage network security policy as their networks grow and become more complex.
It can be quite a challenge to ensure that the right policies are applied at the right control points in order to secure the network.
This task is made even more difficult by having heterogeneous solutions, which complicate matters and make it hard to keep track of everything.
In this article, we will list the best Network Security Policy Management Software.
Comparison of Network Security Policy Management Tools
| Tool Name | Logo | Pricing | Best for | Link |
|---|---|---|---|---|
| Tufin |  | Contact them for a quote. | Deploying Zero Trust Architecture with the industry’s most powerful security policy automation technology. | Learn more |
| ManageEngine Firewall Analyzer |  | Contact them for a quote. | Centralized security management, log analysis, security auditing, and policy enforcement across diverse network devices. | Learn more |
| Algosec |  | Contact them for a quote. | Automating the entire change process. | Learn more |
| Firemon |  | Contact them for a quote. | Automating firewall support operations. | Learn more |
| Palo Alto Networks Panorama |  | Contact them for a quote. | Firewall management. | Learn more |
| Skybox Security |  | Contact them for a quote. | Enterprise cybersecurity, vulnerability, and threat management. | Learn more |

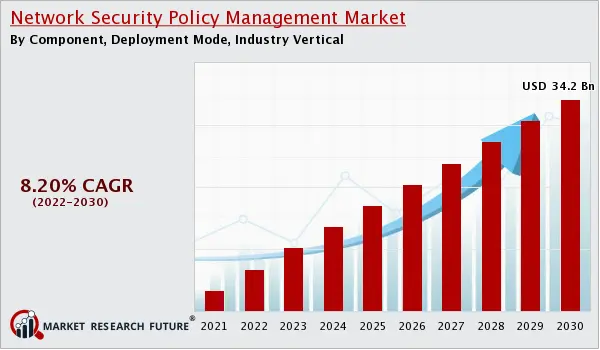
Market Trends: As per MarketResearchFuture, the Network Security Policy Management Market growth is expected to reach USD 34.2 billion by 2030, at a CAGR of 8.20% during the forecast period.
Best Network Security Policy Management Software
Let’s see the best network security policy management tools in the market that helps us in streamlining security policy design and enforcement.
#1. Tufin (Recommended)
Best for deploying Zero Trust Architecture with the industry’s most powerful security policy automation technology.
Tufin is one of the top security policy management software that specializes in automating security policy changes across multiple platforms at the same time; it improves security and compliance. It enables organizations to automate security policy and risk analysis, network configuration management, and access provisioning across their hybrid-cloud, multi-, or on-premises environments.
Security and network professionals have clear visibility and control of all cloud perimeter assets and on-premises assets. Cloud pros can visualize app-level traffic and easily deploy security policies across their cloud-native infrastructures, workloads, and development pipelines.
The Tufin Orchestration Suite supports next-generation firewalls, network switches, load balancers, network layer firewalls, private and public cloud platforms, and routers.
Features:
- It provides both cloud security automation and policy-based network security automation to increase business agility and security.
- Tufin analyzes network traffic logs to identify gaps between reality and your segmentation. It then provides instructions on how to close those gaps.
- This tool provides granular visibility to your network and cloud assets and related security controls. It also offers “what-if” path analysis support and automation for provisioning and security configuration processes. This helps limit human errors and misconfigurations.
- SecureTrack+ feature allows you to create a baseline of traffic allowed and blocked between security zones. You can monitor in real-time for violations to make it easier to implement consistent network segmentation.
- SecureChange+ offers real-time compliance monitoring, as well as a variety of customizable audit reports that are compliant with regulatory standards such as HIPAA, GDPR, PCI-DSS, and NERC-CIP.
Trial: They offer free 30 days trial.
Pricing: Contact them for a quote.
#2. ManageEngine Firewall Analyzer (Recommended)
Best for centralized security management, log analysis, security auditing, and policy enforcement across diverse network devices.

ManageEngine Firewall Analyzer is a comprehensive security information and event management (SIEM) solution specializing in firewall log management, policy analysis, and configuration auditing. It offers a centralized platform to manage a wide range of network security devices, enhancing visibility and control for security professionals.
Features:
- Vendor-agnostic support: Works with leading firewall vendors, like Cisco, Fortinet, Palo Alto Networks, Check Point, and more, for a unified management experience.
- Centralized console: Manage firewalls, VPNs, proxy servers, and IDS/IPS devices from a single platform, streamlining administration tasks.
- Automated rule management: Automate firewall rule creation, modification, and deletion to minimize errors and enforce consistent security policies.
- Real-time log analysis and alerting: Gain real-time insights into network activity, identify suspicious events, and receive instant alerts for potential threats.
- Security auditing and reporting: Conduct comprehensive security audits, uncover vulnerabilities, and generate detailed reports to improve decision-making.
- Change management and configuration analysis: Track firewall configuration changes, identify anomalies, and ensure adherence to security policies.
- Compliance reporting: Generate prepopulated reports that showcase compliance adherence with security regulations like the PCI DSS, NIST, HIPAA, etc.
- Bandwidth monitoring and optimization: Visualize network traffic patterns, identify bandwidth-intensive applications, and optimize resource allocation.
ManageEngine Firewall Analyzer empowers security professionals to manage diverse network security devices, enforce consistent security policies, and gain valuable insights for a stronger security posture.
Trial: ManageEngine offers a free, 30-day trial.
Pricing: ManageEngine follows transparent pricing, which is available on its store page.
#3. Algosec
Best for automating the entire change process.

AlgoSec is the global leader in network security policy management solutions for enterprises, making it possible to be more flexible, secure, and compliant. AlgoSec automates and simplifies network security policy management across SDNs, on-premise firewalls, and public clouds in one place. It allows the most complex organizations in the world to have visibility across their hybrid network, reduce risk and make changes with zero-touch.
AlgoSec Network Security Policy Management Solution prevents outages, minimizes risk, and monitors compliance. This solution integrates with the most trusted vulnerability scanners to map security vulnerabilities to business applications. This gives you the information you need to prioritize and assess risks to your business.
Features:
- It generates audit-ready, pre-populated compliance reports for all major industry regulations, including PCI DSS, SOX, and HIPAA as well as customized corporate policies. This helps to reduce audit preparation time and costs.
- It provides complete management and visibility of firewalls, security controls on private and public clouds, and SDNs like Cisco ACI or VMware NSX. AlgoSec enables you to seamlessly manage and automate your network security policies in a hybrid environment.
- AlgoSec’s network security policy management software simplifies and automates migrating app connectivity to support digital transformation initiatives.
- It automates the process of migrating business apps to the cloud by mapping, discovering, and migrating connectivity configurations with firewalls and security groups.
- This tool is compatible with your existing DevOps tools and practices to help you quickly deploy business applications.
Trial: You can request a free demo.
Pricing: Contact them for a quote.
#4. Firemon
Best for automating firewall support operations.

FireMon is another NPSM tool that solves the complex and dynamic needs of modern enterprise networks through real-time visibility and control over security tools. Security analysts and network security administrators can monitor security using web-based KPI dashboards. This allows them to optimize network device configurations.
FireMon addresses three major challenges: Clean up, Compliance, and Change. FireMon analyzes firewall configurations and validates administrative regulations as well as alarm changes to network access.
The platform uses a contextual approach to monitor and manage network security devices. Traffic flow analysis is its most notable feature. This provides detailed reports about network data flow.
Features:
- FireMon includes access to Lumeta. This risk management tool allows you to monitor all aspects of your network infrastructure. The real-time breach detection tool automatically takes steps to mitigate any attacks you may encounter. Lumeta maps the entire network to find any security gaps and potential leak paths.
- FireMon Security Manager, a firewall and hybrid cloud security policy management platform, is designed to help organizations adapt quickly to changes, manage risk, meet compliance standards, and ensure that they are compliant. Security Manager allows network teams to easily manage complex hybrid networks by standardizing and consolidating cloud security groups and firewall rulesets in one management console.
- FireMon Automation allows you to create automation by providing suggestions and allowing you the ability to add your own procedures. This makes it easy to set up automated processes that are practical and efficient that will improve and enhance your workflow.
- Security Manager’s Policy Planner module is a network security automation tool and orchestration tool. It controls the entire process of change management and provides analysis, recommendations, and compliance checks before implementation. Reviewers can view access paths, vulnerabilities, audit results, and even audit results before pushing a rule live with Policy Planner.
- You can monitor risk in real-time with a complete risk analysis module. It simulates possible damage and scores simulation responses to help you prevent potential threats.
Trial: They offer 30 days free trial.
Pricing: Contact them for a quote.
#5. Palo Alto Networks Panorama
Best for firewall management.

Misconfigurations of firewalls are the most common cause of firewall breaches. Palo Alto NetworksPanorama automates security management by monitoring, configuring, and monitoring. Network security software was designed to simplify IT management for the largest companies.
Administrators can see every packet that passes through their groups at a glance. It aggregates all aspects of firewall configuration and global policy management into one dashboard. It is easy to modify any setting by using a few gestures.
Panorama’s ACC (Application Command Center) technology provides users with an interactive graphical view of every application running on your network. Built-in network firewall software allows the app to connect with Palo Alto Networks (PAN) deployed machines.
Features:
- Panorama provides network security management with one security rule base that covers firewalls, threat prevention URL filtering, application awareness, user identity, user identification, file blocking, access control, data filtering, and more.
- It displays interactively graphical information about applications, URLs, and threats as well as data files, patterns, and other data that traverse your Palo Alto Networks firewalls. You can now easily see network activity, threat activity, and blocked activity. Additionally, you can create custom views of historical and current data.
- Panorama’s automated correlation engine reduces data clutter, so you can quickly identify compromised hosts and spot malicious behavior.
- It allows you to organize firewall management using hierarchical device groups, dynamic addresses, user groups, role-based access control, and policy tags. Pre-configured templates reduce the time required to create new rule sets.
- This solution is easy to scale as your firewall deployment expands – one pair of high-available appliances can manage up to 5,000 virtual, container as well as physical Palo Alto Networks Firewalls.
Pricing: Contact them for a quote.
#6. Skybox Security
Best for enterprise cybersecurity, vulnerability, and threat management.

Skybox Security is the most comprehensive cybersecurity platform in the market to address security issues within large and complex networks. Skybox Security Suite integrates with 130 security and networking technologies. This gives you complete attack surface visibility and the context to take informed action.
Skybox Vulnerability Control feature provides a focused, systematic approach to vulnerability management that delivers intelligent risk reduction. Vulnerability Control provides total visibility into the attack surface and continuous threat intelligence. It analyzes the risk within the context of the organization’s vulnerabilities, network, and exploits in nature.
Skybox Threat Manager consolidates threat intelligence and analyses and prioritizes advisories within the context of an organization’s attack surface. It analyzes the possible impact of a threat automatically and guides remediation so that organizations can quickly respond to any imminent threats.
Features:
- You can centrally manage traditional, next-gen, and virtual firewalls as well as secure access service edge solutions (SASE) from multiple vendors. You can easily manage east-west and south-south traffic quickly and effectively.
- Detect rule conflicts and access policy violations. Confirm compliance with firewall access rules and configurations. Skybox Threat Intelligence can help you identify and fix potential vulnerabilities in your firewalls.
- The firewall assurance feature allows you to identify unused rules, redundancies, and rules that can be simplified. This will improve firewall security and speed up troubleshooting.
- The Change Manager workflows feature automates rule implementation and the surrounding analysis required to ensure that every rule is compliant and secure. It verifies that the changes implemented to match the original request for change. This helps to ensure that all changes are authorized.
- Change Manager workflows for creating, recertifying, and de-provisioning firewall rules help to maintain compliance, close security gaps, and minimize vulnerability exposures.
Trial: Contact them for a demo.
Pricing: Contact them for a quote.
#7. Cisco Defense Orchestrator
Best for writing a policy once and enforcing it consistently across multiple security devices.

Cisco Defense Orchestrator is a cloud-based security policy management solution that enables you to create consistent security policies across multiple Cisco security platforms. It allows you to manage all policies for your Cisco security products. It’s a cloud-based app that reduces complexity and keeps your organization safe from the latest threats.
The platform is capable of managing security policies in multiple environments including Cisco Adaptive Security Appliance, Cisco Firepower, Meraki MX, and Amazon Web Services.
Continuous scanning of each environment allows the product to detect any changes in supported devices. Defense Orchestrator quickly identifies inconsistencies and misconfigurations once a device has been added to its inventory list. The platform can identify performance-enhancing changes, which allows you to improve your network and security in one solution.
Features:
- Cisco Defense Orchestrator, like other NSPMs, offers easy deployment of new devices. The platform automatically detects new hardware, and administrators don’t have to travel to their site or have firewalls shipped for configuration.
- Firmware updates, image upgrades, and configuration changes are all easily sent out to any device, per group, or worldwide. This flexibility is ideal for large environments and allows MSPs the ability to tailor their settings to each client.
- Cisco offers detailed insight and alerts on the backend based on changes in the environment. This tool can detect ransomware and DDoS attacks as well as insider threats. It even allows for crypto mining within the network.
- Standard policy templates allow you to deploy new devices quicker by providing consistent protection across your Cisco environment. As your organization grows, new deployments inherit the most current policies.
Trial: Contact them for a demo.
Pricing: Contact them for a quote.
#8. McAfee ePolicy Orchestrator
Best for centralized security management.

McAfee Security Orchestrator (McAfee ePO) aims to offer a single web-based platform that allows you to access all of your configuration management tools and security tools. It currently supports both on-premises and AWS cloud deployments. There is also a SaaS version that McAfee staff manages.
=It offers flexible and automated management capabilities that allow you to identify, manage and respond to security threats and issues.
McAfee ePO software will direct security alerts and security responses based on your environment’s type and severity. You can also create automated workflows between your IT and security systems to quickly resolve any outstanding issues. You can save time and money by creating a more efficient security program. McAfee ePO software reduces the complexity and cost of security management.
Features:
- Visually McAfee has a very clean dashboard. It’s easy to use and clear. Pre-configured reports display metrics such as unresolved malware, software status, and recent configuration changes all in one place. You can also add devices manually or via auto-discovery, giving you more control over how devices are collected. This is especially useful in a BYOD environment.
- It does a great job of highlighting key issues and suggesting solutions. The platforms include pre-configured automated solutions that are tailored to specific compliance standards and best practices.
- The ePolicy Orchestrator System Tree organizes managed system units in order to monitor, assign policies, schedule tasks, and take action. These units are known as groups and are managed by Global Administrators or other users who have the right permissions. Systems and other groups can be included in groups.
- McAfee ePO is the central repository for McAfee product updates and installations. The modular design and flexibility of ePolicy Orchestrator make it possible to add new products as extensions.
Pricing: Contact them for a quote.
#9. Microsoft System Center
Best for simplifying the deployment, configuration, management, and monitoring of your infrastructure.

Microsoft System Center delivers a single experience of management across cloud, on-premises, and service provider environments. It covers critical infrastructure management, DevOps, resource provisioning, configuration monitoring, automation, service management, and endpoint protection.
It improves performance and usability by providing a simple, intuitive management console. The user experience is improved by pre-defined templates, single-click features, alert tuning, and better IT control to enable more efficient configuration management and automation.
System Center allows the IT team to manage almost any infrastructure platform, including on-premises, Azure, and Amazon Web Services (AWS). It also supports Windows Server, Linux, or VMware.
Features:
- It can manage a heterogeneous environment with multiple operating systems and hypervisors. It can be combined with Windows Server to create a software-defined database center (SDDC). This allows you to manage, deploy, and configure your infrastructure resource, including storage, computing, security, and network.
- System Center simplifies the provisioning of infrastructure resources in the data center or on the cloud. These functions include provisioning resources such as virtual machines, SAN devices, and network devices.
- System Center allows the deployment and management of storage clusters using Storage Spaces Direct (S2D) in both disaggregated or hyper-converged topologies. Storage Spaces Direct (S2D) is a Microsoft Windows Server feature that allows the creation of highly available, scalable storage systems with local storage.
- System Center Virtual Machine Manager allows you to deploy and manage virtual machines across multiple hypervisor platforms, including VMware ESXi hosts. It integrates directly with VMware vCenter Server. VMM allows you to manage, provide and distribute resources from multiple hypervisors as well as make resources available for private cloud deployments. All this is done from a common user interface (CLI) and command-line interface.
Trial: They offer a 180-day trial.
Pricing: Contact them for a quote.
#10. SolarWinds Network Configuration Manager
Best for network compliance and automation.

SolarWinds Network Configuration Manager (NCM) is a network configuration management tool that is designed to automate, back up, and manage configurations. It can locate and roll back previous configurations quickly to ensure that your network is secure.
SolarWinds NCM allows you to quickly create an accurate inventory of all your network devices. You can use network scanning and discovery for the most current information about all network devices.
It can automate and centralize how you track and review devices throughout your network. This includes multi-vendor devices. A unified dashboard allows you to monitor configurations, backups, and changes.
Features:
- It allows you to create and maintain a fully automated configuration archive that is reliable for most routers and switches, including Cisco, Juniper, Adtran, Brocade and Dell, Extreme Networks as well as HP, Palo Alto, and Synoptics. NCM can also backup firewall configurations of Palo Alto, SonicWALL, Palo Alto, and Fortinet firewalls.
- It gives you real-time information on network configuration changes, including who and what they were. NCM offers automated config backup capabilities that will ensure that your network configuration archive remains up-to-date and is easily accessible.
- It provides a strong set of tools to manage baseline configurations. Multiple comparison views-like config-to-config and baseline-to-config–can provide actionable insights into potential vulnerabilities and inconsistencies within your network brought on by changes made to configuration items. NCM allows you to quickly find the problem areas, regardless of how large your network is.
- Its network audit tools make it easier to identify inconsistent or unauthorized configuration modifications, non-compliant devices, failed backups, and other issues. NCM audits provide historical and real-time insight into user activity to determine if there have been any vulnerable configuration gaps or unauthorized changes.
Trial: They offer a fully functional 30 days trial.
Pricing: Pricing starts at $1,738. Contact them for a quote.
FAQ – Network Security Policy Management Software
Why Do You Need Firewall and Network Security Management
Firewall and Network security management are key components of any organization’s network infrastructure. They are essential for protecting against costly misconfigurations, gaining visibility into your full network (not just firewalls), and maintaining compliance. By having clear processes in place and making sure they’re followed, you can keep your network safe while also making it simpler to manage overall security.
When it comes to cyber security threats, prevention is always better than cure. Firewall and Network Security Management are the cornerstone of any reliable security program.
What is a Firewall?
A firewall is a device that acts as a barrier between your internal network and the internet, allowing only authorized traffic to pass through. Firewalls can be used to protect against malicious attacks such as denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks, and they can also provide access control by allowing only certain ports, protocols, or services.
What Is Network Security Policy Management?
NSPM aka Network Security Policy Management provides data centers with an array of services that simplify complex network security operations such as firewall policy management, change workflows for complex policies, compliance audits, and managing multiple firewall vendors.
Network security policy management provides visibility into these dynamic environments and makes it easier to implement policy changes when necessary.
The main goals of a network security policy are to protect the organization’s data, networks, systems, and devices from external and internal threats. It also helps to ensure the safety of users and their data, as well as compliance with regulatory requirements.
Thus, NSPM is a critical component of any organization’s security strategy. When implemented correctly, NSPM can provide significant benefits in terms of improved security by identifying and addressing vulnerabilities, reduced costs associated with data breaches, enhanced compliance by meeting all relevant regulatory requirements, and improved operational efficiency by automating repetitive tasks.
What’s Network Security Policy Management Software (NSPM Software)?
NSPM software provides users with the suite of tools needed to follow compliance policies and procedures related to network security and firewall management. These tools give the ability to create and document operational processes for network security management as well as aid in orchestration.
NSPM software not only provides tools for auditing networks and documenting policy changes, but automating security operations as well. Companies can use NSPM software to ensure compliance with network policies while keeping endpoints, data, and networks secure. These helpful tools identify and get rid of unneeded or outdated security policies while streamlining security operations.
How to Choose the Best Network Security Policy Management (NSPM) Software?
NSPM solutions have many features. You must choose the one that best suits your needs.
When purchasing an NSPM solution, it is important to evaluate the software’s ability to integrate with all apps and endpoint devices as well as equipment and technologies. The software should be capable of automatically creating and implementing policies.
It must also comply with data protection standards. It should provide log management and alerting capabilities. This will allow you to track policy changes. A free trial or demo is a great way to test the product before you commit to long-term investments.
We also recommend you speak with an IT professional in order to identify the most critical features for your company.
Research Process – NSPM Tools
- Total time we spent on evaluating these tools: 48
- Total tools evaluated: 12
- Total tools finalized: 10
We spent 48 hours evaluating and researching 12 different NSPM Tools. We looked for features that should be available in an ideal NSPM Software.
Based on our research, we believe that Tufin is one of the Best Network Security Policy Management Software in the market. Also, we believe ManageEngine, Algosec, Firemon, and Palo Alto Networks Panorama do a good job.
Conclusion – NSPM Software
Network Security Policy Management Software (NSPM) is the most important software that you need.
Today’s NSPM Software is extremely versatile and remains a low-cost investment due to strong competition. Since there are many options for NSPM, it can be difficult to find the right NSPM tools for your company.
We hope this list of top Network Security Policy Management Software (NSPM) lets you pick the best for your needs.
Related posts:
- Best Skybox Security Competitors
- Best Tufin Competitors
- Best Algosec Competitors
- Best Firemon Competitors
- Firewall Audit Software
- Network Segmentation Software







