Security Testing Tutorial: A Comprehensive Guide to Safeguarding Software

In today’s digital landscape, where cyber threats are constantly evolving, security testing has become an indispensable part of the software development lifecycle. As a senior quality assurance engineer, I’ve witnessed firsthand the critical role that robust security testing plays in safeguarding applications and protecting sensitive data. This comprehensive tutorial aims to equip you with the knowledge and skills necessary to implement effective security testing strategies in your projects.
Throughout this guide, we’ll explore various types of security testing, delve into proven methodologies, and examine essential tools and techniques. Whether you’re a seasoned QA professional looking to expand your expertise or a developer aiming to integrate security best practices into your workflow, this tutorial will provide valuable insights to enhance your software’s resilience against potential threats.
What is Security Testing in Software Testing?
Security testing is a type of software testing that aims to uncover vulnerabilities, threats, and risks in a software application, ensuring that the system remains secure from potential attacks. It involves a detailed analysis of the application’s security mechanisms and evaluates their effectiveness in data protection and maintaining functionality as intended.
The ultimate goal of security testing is to identify any weaknesses that could be exploited by malicious entities and to rectify these issues before they can be leveraged in real-world scenarios.
By performing security testing, organizations can safeguard their applications, preserving the confidentiality, integrity, and availability of their systems and data.
We can do security testing using both manual and automated security testing tools and techniques.
Pro Tip: Many organizations focus on security testing for newly deployed or developed software, hardware, and network or information system environments. However, it is highly recommended to incorporate security testing into the information system audit process for existing environments. This approach helps identify potential security risks and assists developers in addressing them.
What are the major focus areas in Security Testing
The following are the four major focus areas to be considered in terms of testing the security of a web application.
- Vulnerability Scanning: This process involves using automated tools to scan your application for known vulnerabilities. These tools can quickly identify flaws and weaknesses in your system, such as outdated software, misconfigurations, and potential entry points for attackers. Regular scanning helps in keeping the application secure by identifying issues before they are exploited.
- Penetration Testing: Also known as ethical hacking, penetration testing simulates real-world attacks on your system to find vulnerabilities that could be exploited. Testers attempt to break into the system, much like a malicious hacker would, but without causing harm. This helps in understanding how an attacker could gain access and what damage they might do.
- Security Auditing: Security auditing involves a detailed examination of the application’s code, configurations, and security policies. This can be done manually or through automated tools. The goal is to ensure that all security measures are up to date and that there are no hidden vulnerabilities.
- Risk Assessment: Risk assessment identifies the risks that could impact the application’s security. This involves evaluating the likelihood and potential impact of different types of attacks. By understanding the risks, you can prioritize security measures and focus on protecting the most critical areas first.
- Security Code Review: This involves a thorough review of the application’s code to find security flaws. Developers and security experts work together to identify issues such as insecure coding practices, hard-coded secrets, and other vulnerabilities that could be exploited.
- Configuration Testing: This area focuses on ensuring that the application’s configurations are secure. This includes checking server settings, network configurations, and access controls. Proper configuration is crucial for preventing unauthorized access and ensuring system stability.
- Compliance Testing: Ensuring compliance with industry standards and regulations is another key focus area in security testing. This involves verifying that the application meets requirements such as GDPR, HIPAA, and PCI-DSS. Non-compliance can lead to penalties and legal issues, so it’s crucial to ensure that your application adheres to all relevant standards.
- Incident Response Testing: It’s important to have a plan for responding to security incidents. Incident response testing involves simulating security breaches to evaluate how well the incident response plan works. This helps in identifying gaps in the plan and preparing the team to handle real-world incidents effectively.
By concentrating on these major focus areas, security testing ensures a comprehensive approach to safeguarding your application from potential security threats. Each area plays a critical role in building a robust security posture, making your application more resilient to attacks.
Goals of Security Testing
Security testing aims to identify and address any vulnerabilities in a software application, ensuring that it is protected against potential threats and attacks. The primary goals of security testing are:
- Confidentiality: This ensures that sensitive information is not disclosed to unauthorized individuals or systems. Security testing helps to confirm that data is properly encrypted and that access controls are in place to protect personal and confidential information.
- Integrity: This goal is focused on ensuring that data remains accurate and unaltered during its lifecycle. Security testing verifies that only authorized users can modify data and that any changes are properly logged and traceable.
- Availability: Ensuring that the software is available and accessible when needed is crucial. Security testing checks for vulnerabilities that could lead to denial-of-service attacks or other issues that might impede access to the application.
- Authentication: This ensures that users are who they claim to be. Security testing involves verifying that robust authentication mechanisms, like passwords or biometric data, are effective in preventing unauthorized access.
- Authorization: This goal is about ensuring that users have the appropriate access levels. Security testing evaluates whether the access control policies correctly enforce role-based restrictions, allowing users to perform only those actions they are permitted to do.
- Non-repudiation: This ensures that users cannot deny their actions. Security testing verifies mechanisms such as digital signatures and transaction logs, which guarantee that actions within the system can be traced back to the responsible individuals.
By addressing these goals, security testing helps protect applications from various security risks, ensuring that they are reliable and trustworthy for users.
What are the principles of Security Testing?
It aims at covering following basic security components
- Authentication
- Authorization
- Availability
- Confidentiality
- Integrity
- Non-repudiation
Let’s delve deeper into these key principles to understand their significance in security testing:
#1. Authentication
Authentication is the process of verifying who you are. Just as you use a key to enter your home, authentication methods – such as passwords, fingerprint scans, or security tokens – verify your identity before granting access. This step is crucial in ensuring that sensitive systems and data are protected from unauthorized access.
#2. Authorization
Once a user is authenticated, authorization determines what they are allowed to do. Imagine being in a library where you have access to certain sections based on your membership level. Similarly, systems use authorization to control access levels, ensuring users can only access information and perform actions that they have permission for.
#3. Availability
Availability means that systems and data are accessible when needed. It’s like having a 24/7 store – you expect it to be open whenever you want to buy something. This principle ensures that critical resources are available to authorized users without interruption. Techniques like redundancy, regular maintenance, and robust backup plans help in achieving high availability.
#4. Confidentiality
Confidentiality is all about keeping sensitive information away from those who shouldn’t have access to it. Imagine your personal diary – you wouldn’t want just anyone to read it. In the same way, confidentiality ensures that only authorized people can access sensitive data, protecting it from prying eyes. This is achieved through encryption, access controls, and other security measures.
#5. Integrity
Integrity ensures that the information remains accurate and unaltered during its lifecycle. Think of it like a signed contract; you wouldn’t want someone to change its terms after it’s been signed. In the digital world, integrity means making sure data cannot be tampered with by unauthorized individuals. Techniques like checksums and hash functions help in maintaining data integrity.
#6. Non-repudiation
Non-repudiation ensures that once a transaction has occurred, the parties involved cannot deny it. Think of it like getting a receipt when you buy something; it serves as proof of the transaction. In digital terms, this involves using digital signatures and logs that provide verifiable evidence of actions taken, ensuring accountability and traceability.
Understanding and implementing these principles helps in creating robust security measures that protect an organization’s systems and data from potential threats.
Why Security Testing is Important?
Software security testing is important due to the increase in the number of privacy breaches that websites are facing today. In order to avoid these privacy breaches, software development organizations have to adopt this testing in their development strategy based on testing methodologies and the latest industry standards.
Some of the reasons why it is important are as follows
- Protects Sensitive Information: Security testing helps safeguard personal and financial information from hackers.
- Prevents Data Breaches: By finding and fixing security vulnerabilities and weaknesses in the system early, we can stop data leaks before they happen
- Saves Money: Avoiding security breaches saves the company from costly losses and fines.
- Maintains Reputation: Keeping systems secure helps maintain the trust customers have in the company.
- Ensures Compliance: Security testing helps make sure the company follows laws and industry standards.
- Stops Attacks: It identifies possible weaknesses that hackers might exploit and fixes them.
- Improves System Reliability: Regular testing ensures that the systems are reliable and can handle attacks, making them more trustworthy.
It is important to adopt a Security Process in each and every phase of SDLC.
- Requirement Phase: Security analysis of all the requirements
- Design Phase: Implementation of Test Plan including Security tests.
- Code & Unit Testing: Security White Box Testing
- Integration Testing: Black Box Testing
- System Testing: Black Box Testing & Vulnerability Scanning
- Implementation of System Testing: Penetration Testing & Vulnerability Scanning
- Support: Impact Analysis
Top Vulnerabilities
Security tests include testing for software vulnerabilities such as
- SQL Injection
- Cross-Site Scripting (XSS)
- Session Management
- Broken Authentication
- Cross-Site Request Forgery (CSRF)
- Security Misconfiguration
- Failure to Restrict URL Access
- Secure Data Exposure
- Insecure Direct Object Reference
- Missing Function Level Access Control
- Using Components with Known Vulnerabilities
- Unvalidated Redirects and Forwards
What are the Advantages of Security Testing?
Security testing offers several advantages that are essential for protecting your application from potential threats. Here are some key benefits:
- Enhanced Security: Security testing helps identify and fix vulnerabilities before they can be exploited by hackers. By discovering these issues early, you can protect sensitive data and prevent unauthorized access.
- Compliance Assurance: Many industries have strict regulations and standards that organizations must follow. Security testing ensures your application meets these requirements, helping you avoid legal issues and penalties.
- Improved Customer Trust: When users know that their data is safe with you, they are more likely to trust your application. Security testing enhances your reputation by showing that you take their privacy and security seriously.
- Cost Savings: Fixing security issues during the development phase is usually much cheaper than dealing with a security breach later. Security testing can save you money by preventing costly incidents.
- System Stability: Security testing not only protects your application but also helps ensure its stability. Proper configurations and secure coding practices contribute to a more reliable and resilient system.
- Quick Incident Response: By testing your incident response plan, you can handle security breaches more effectively. This preparation minimizes damage and helps you recover quickly from any potential attack.
- Continuous Improvement: Regular security testing keeps your security measures up to date. As new threats emerge, ongoing testing ensures that your application remains secure over time.
What are the Disadvantages of Security Testing?
While security testing is essential for protecting applications and data, it also comes with some disadvantages. Understanding these drawbacks can help you prepare better and make informed decisions.
- Expense: Conducting thorough security tests can be costly. Small businesses or startups might find it challenging to allocate a budget for comprehensive security testing, which often requires specialized tools and expertise.
- Time-Consuming: Security testing can be a lengthy process. Finding and fixing vulnerabilities takes time, which could delay the development timeline. This is especially critical for projects with tight deadlines.
- Resource-Intensive: Effective security testing requires skilled cybersecurity professionals. Hiring these experts or training your existing team can be resource-intensive. Additionally, running extensive tests can consume significant computational resources.
- False Positives and Negatives: Sometimes, security tests might produce false positives (alerting to issues that aren’t real) or false negatives (failing to detect actual vulnerabilities). This can result in wasted effort addressing non-existent problems or leaving real threats unnoticed.
- Complexity: Security testing can be complex, especially for large or highly integrated systems. Testing all components thoroughly is challenging, and missing even a small vulnerability can have significant repercussions.
- System Disruptions: Some security tests, particularly those that simulate attacks, might disrupt normal system operations. This can affect the availability and performance of your application temporarily.
What are the Types of Security Testing
Security testing is crucial in identifying weaknesses in a system and ensuring data integrity and protection against breaches. Below are detailed explanations of seven main types of security testing:
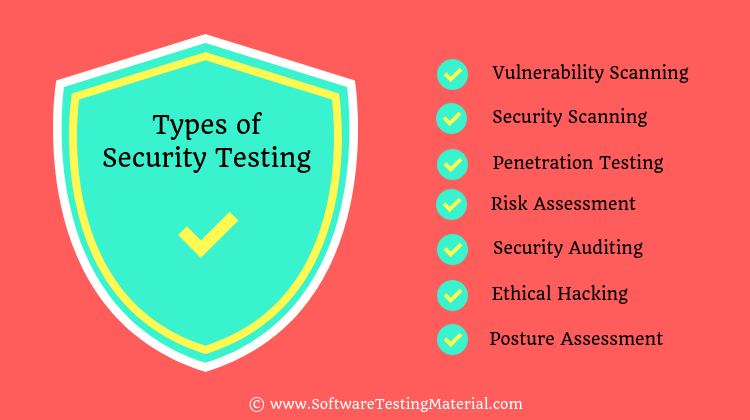
#1. Vulnerability Scanning
Vulnerability scanning (aka vulnerability assessment) involves automated vulnerability scanning tools that scan systems, networks, or applications to identify known vulnerabilities. These tools compare the scanned results with a database of existing vulnerabilities to flag security issues that need addressing.
#2. Security Scanning
Security scanning typically encompasses both network and system scans to discover vulnerabilities that might be exploited by hackers. Unlike vulnerability scanning, it also involves the analysis, assessment, and categorization of findings to guide remediation efforts.
#3. Penetration Testing
Penetration testing, also known as pen testing, involves simulating cyberattacks on a system to identify vulnerabilities that could be exploited. Ethical hackers carry out these tests either manually or with automated security tools to assess the impact of potential real-world attacks and strengthen the system. The process is repeated until the system is negative to all identified threats. Pen testing can be categorized into three approaches: manual penetration testing, automated penetration testing, and a hybrid of both methods.
Read more on Pen Testing Techniques
#4. Risk Assessment
Risk assessment is the process of identifying, evaluating, and prioritising risks to organisational assets. This involves understanding potential threats, determining the likelihood of these threats, and assessing the impact on the organisation. The goal is to manage and mitigate risks effectively.
#5. Security Auditing
Security auditing is a comprehensive review of an organisation’s information system to ensure compliance with internal policies and external regulations. It includes evaluations of organisational policies, asset management, operational processes, and governance measures.
#6. Ethical Hacking
Ethical hacking entails legally breaking into computers and devices to test an organisation’s defenses. Ethical hackers use the same techniques as malicious hackers but with permission from the organisation to uncover security flaws and help mitigate them.
Read more: Types of Hackers
#7. Posture Assessment
Posture assessment combines information from various security assessments, including vulnerability scans, risk assessments, and compliance audits, to provide an overall view of an organisation’s security stance. This helps in understanding the effectiveness of current security measures.
Some other types of Security Testing are as follows
#8. Application Security Testing
Application security testing focuses on identifying security flaws within software applications. It includes activities like code review, penetration testing, and dynamic and static application security testing (DAST and SAST) to uncover vulnerabilities during the software development lifecycle.
#9. Network Security Testing
Network security testing involves assessing a network’s potential vulnerabilities before attackers can exploit them. This includes testing firewalls, routers, and other network components to ensure they are configured securely and can withstand attacks.
#10. Social Engineering Testing
Social engineering testing evaluates an organisation’s susceptibility to social engineering attacks, where attackers manipulate individuals into divulging confidential information. This often includes phishing simulations and other attempts to trick employees into revealing sensitive information.
#11. Configuration Scanning
Configuration scanning reviews system setups and configurations to ensure they comply with security best practices. This includes checking for misconfigurations that could lead to vulnerabilities, such as default passwords, open ports, and improper access controls.
Understanding these types of security testing allows organisations to implement comprehensive security strategies to protect against various threats and vulnerabilities effectively.
Security Test Cases and Scenarios
#1. Authentication
Test Case #1: Valid Login
Description: Verify that users can log in with valid credentials.
Steps:
- Open the login page.
- Enter a valid username and password.
- Click the “Login” button.
Expected Result: User is successfully logged in and redirected to the dashboard.
Test Case #2: Invalid Login
Description: Verify that users cannot log in with invalid credentials.
Steps:
- Open the login page.
- Enter an invalid username and/or password.
- Click the “Login” button.
Expected Result: User is not logged in and an error message is displayed.
Test Case #3: Password Policy Enforcement
Description: Ensure password meets complexity requirements.
Steps:
- Open the registration page.
- Enter a password that does not meet the complexity criteria (e.g., no uppercase letters).
- Attempt to submit the form.
Expected Result: An error message is displayed indicating the password policy requirements.
Test Case #4: Account Lockout After Multiple Failed Attempts
Description: Verify the account gets locked after a set number of failed login attempts.
Steps: Attempt to log in with an invalid password multiple times (e.g., 5 attempts).
Expected Result: The account is locked, and the user is notified accordingly.
#2. Input Validation
Test Case #1: Cross-Site Scripting (XSS) Prevention
Description: Ensure that the application is protected against XSS attacks.
Steps:
- Navigate to a form (e.g., comment box, search field).
- Enter a script as input (e.g., `<script>alert(‘XSS’);</script>`).
- Submit the form.
Expected Result: The input is sanitized, and the script is not executed.
Test Case #2: SQL Injection Prevention
Description: Verify that the application is protected against SQL injection.
Steps:
- Go to a form that interacts with a database (e.g., login form, search bar).
- Enter an SQL injection string (e.g., `’ OR ‘1’=’1’`).
- Submit the form.
Expected Result: The input is sanitized, and no SQL injection occurs.
Test Case #3: Input Length Validation
Description: Ensure input fields enforce maximum length constraints.
Steps:
- Navigate to a form field (e.g., username or description field).
- Enter a string that exceeds the maximum allowed length.
- Submit the form.
Expected Result: An error message is displayed indicating the input exceeds the maximum length.
#3. Business Logic
Test Case #1: Verify Order Discount Application
Description: Ensure discounts are applied correctly based on business rules.
Steps:
- Add items to the shopping cart meeting the discount criteria.
- Proceed to checkout.
Expected Result: The appropriate discount is applied to the total amount.
Test Case #2: Unauthorized Access to User Data
Description: Verify users cannot access data that they are not authorized to view.
Steps:
- Log in as a regular user.
- Attempt to access another user’s data through URL manipulation or any other means.
Expected Result: Access is denied, and an error message is displayed.
Test Case #3: Transaction Integrity Check
Description: Ensure transactions are processed correctly and in their entirety.
Steps:
- Initiate a transaction (e.g., money transfer or purchase).
- Interrupt the transaction process (e.g., close the browser).
- Check the status of the transaction.
Expected Result: The transaction is either completed correctly or rolled back to prevent half-completed actions.
These detailed security test cases and scenarios aim to ensure the safety, reliability, and integrity of your application, fortifying it against common vulnerabilities.
Types of Security Testing Tools
There are various security testing tools designed to tackle different aspects of vulnerability assessment and application protection. These tools help in identifying, managing, and mitigating potential threats across software and network environments. Below are some of the most important types of security testing tools:
#1. Static Application Security Testing (SAST)
SAST tools analyze an application’s source code, bytecode, or binary code to find security vulnerabilities. These tools can be integrated early in the development process, allowing developers to identify and fix issues before they make it into production. SAST tools are useful for detecting common coding errors, such as SQL injection, cross-site scripting (XSS), and buffer overflows.
#2. Dynamic Application Security Testing (DAST)
Unlike SAST, DAST tools test the running application from the outside. These tools simulate external attacks on an application while it is running to identify potential vulnerabilities. DAST is effective in uncovering issues like authentication flaws, injection attacks, and runtime vulnerabilities that SAST might miss. This type of testing is usually performed after the application has been deployed.
#3. Interactive Application Security Testing (IAST)
IAST combines elements of both SAST and DAST by analyzing the application from the inside while it is running. These tools monitor the application in real-time, providing a detailed view of how the application behaves and interacts with its environment. IAST tools can identify complex vulnerabilities that are difficult to detect through traditional methods, offering more accurate and actionable findings.
#4. Software Composition Analysis (SCA)
SCA tools focus on analyzing the third-party components and libraries used within an application. These tools identify any known vulnerabilities in open-source or commercial components, ensuring that all dependencies are secure. SCA helps organizations manage the risks associated with using third-party software, providing insights into licensing compliance and potential security issues.
#5. Mobile Application Security Testing (MAST)
MAST tools are designed specifically for mobile applications, addressing the unique challenges and vulnerabilities present in mobile environments. These tools can perform both static and dynamic analyses, checking for insecure coding practices, data leakage, and other mobile-specific security issues. MAST ensures that mobile applications adhere to best practices and are resistant to attacks.
#6. Runtime Application Self-Protection (RASP)
RASP tools are embedded within the application to provide real-time protection during runtime. These tools monitor the application’s behavior and intercept potentially malicious actions. If an attack is detected, RASP can take immediate actions, such as terminating the session or blocking the attacker. This proactive approach helps safeguard applications from being exploited in real-time.
By leveraging these security testing tools, organizations can effectively reduce the risk of vulnerabilities and improve their overall security posture.
Techniques for security testing
Techniques/Methodologies followed in Security Testing are as follows.
#1. Black Box Testing
Black Box Testing is a technique where the tester evaluates the software without knowing the internal workings of the application. The focus is on identifying vulnerabilities in the system’s external interfaces and user inputs. This method simulates the perspective of an external attacker, making it effective at identifying vulnerabilities that could be exploited without needing insider knowledge. Common approaches include penetration testing, fuzz testing, input validation testing and functional testing of exposed APIs and endpoints.
#2. White Box Testing
White Box Testing, also known as Clear Box or Glass Box testing, is a technique where the tester has full access to the internal workings of the application. Testers look closely at the code to find security flaws such as logic errors, coding issues, and design weaknesses. This detailed examination can reveal hidden vulnerabilities that might not be apparent from an external perspective. Common methods used include code review, static code analysis, where the code is examined without running it, and security code audits.
#3. Grey Box Testing
Grey Box Testing combines elements of both Black Box and White Box testing. In this method, testers have partial knowledge of the internals of the application, such as architectural diagrams, database schemas, or some source code. The focus is on identifying vulnerabilities both from an external perspective and from a limited internal perspective, simulating an attack by someone with partial insider knowledge. This balanced approach makes Grey Box Testing very effective, as it provides depth without the complete transparency of White Box Testing. Techniques often used includes both black box techniques and white box techniques such as code reviews and security audits of known components.
#4. Tiger Box Testing
Tiger Box Testing is a specialized form of penetration testing where a physical hacker station, often called a “Tiger Box,” is used to attack a network. Testers mimic the actions of skilled hackers to find vulnerabilities in hardware and network systems. This method is particularly effective for assessing the security of network infrastructures and hardware devices. Techniques includes network attacks, web application attacks, social engineering, and other advanced penetration testing methods using the preconfigured tools on the Tiger Box.
Security Testing Tools
To find the flaws and vulnerabilities in a web application, there are many free, paid, and open-source tools available in the market. We know that the advantage of open source tools is that we can easily customize it to match our requirements. We are here to showcase some of the top 12 open-source security testing tools.
We use these testing tools for checking how to secure a website or web application is.
Open Source Security Testing Tools
Open source security testing tools are essential for identifying vulnerabilities in applications without the need for expensive licensing fees. Three widely recognized tools in this category are Zed Attack Proxy (ZAP), Wfuzz, and Wapiti.
- Zed Attack Proxy (ZAP): ZAP is a popular tool developed by the OWASP (Open Web Application Security Project). It helps security testers by providing automated scanners and a variety of tools that can manually find security issues in web applications. ZAP is user-friendly, making it suitable for those new to security testing as well as seasoned professionals. It features a powerful REST API, allowing integration with other tools and services. ZAP can be used to intercept and modify HTTP and HTTPS traffic, facilitating the detection of vulnerabilities such as SQL injection and cross-site scripting (XSS).
- Wfuzz: Wfuzz is a web application brute forcer, which is designed to identify security flaws in web applications by sending a large number of HTTP requests to a target. Unlike general-purpose vulnerability scanners, Wfuzz focuses on the repetitive tasks of security testing, like brute forcing parameters, directories, and forms. It’s highly configurable, with a range of options to customize the attack to your needs, and it supports a variety of injection techniques, making it a very versatile tool for testing web application security.
- Wapiti: Wapiti is a tool that performs “black-box” scans (testing without knowing the internal workings) to discover vulnerabilities in web applications. It operates by crawling the web pages of the target site and testing for issues such as file disclosure, database injections, and Cross-Site Scripting (XSS). Wapiti automatically injects payloads to look for vulnerabilities, making it an efficient choice for comprehensive testing. Its ease of use and effectiveness make it very appealing for security auditors who need to identify and fix security flaws quickly.
These open-source tools provide robust capabilities for security testing, making them invaluable for developers and security professionals alike. They help ensure that web applications remain secure against potential threats, contributing significantly to overall cybersecurity efforts.
Commercial Security Testing Tools
- GrammaTech: GrammaTech is a leading commercial security testing tool offering static code analysis to detect vulnerabilities in software. Its advanced analysis capabilities help identify code defects, security flaws, and compliance issues early in the development process. GrammaTech’s tools integrate proficiently with various development environments and continuous integration pipelines, making it a valuable asset for developers aiming to produce secure code. Moreover, it provides detailed reports that are easy to understand, allowing teams to quickly address any discovered vulnerabilities.
- AppScan: IBM’s AppScan is a comprehensive security testing tool designed to find vulnerabilities in web applications and services. It performs both static and dynamic analysis to uncover security issues, ranging from common weaknesses like SQL injection to more complex threats. AppScan comes with a user-friendly interface and offers features such as automated scanning, detailed vulnerability assessment, and remediation guidance. Additionally, it supports extensive customization and integrates seamlessly with existing workflows, making it ideal for secure application development.
- Veracode: Veracode is another prominent commercial security testing solution, known for its cloud-based platform that provides static, dynamic, and software composition analysis. What sets Veracode apart is its ability to scan for vulnerabilities at different stages of the application lifecycle, ensuring continuous security assessment. Veracode offers comprehensive reporting and actionable insights, which help development teams quickly fix vulnerabilities and improve their security posture. The platform’s ease of use and ability to integrate with development environments make it convenient for organizations aiming to streamline their security testing processes.
These commercial tools provide essential features and capabilities to maintain and enhance application security, ensuring that software products are robust and resistant to cyber threats. Their sophisticated analysis, integration options, and easy-to-understand reporting make them indispensable in the toolkit of any security-conscious development team.
To learn more you can also check the OWASP (Open Web Application Security Project) site.
Conclusion
As we conclude this security testing tutorial, it’s crucial to remember that security is not a one-time effort but an ongoing process. The landscape of cyber threats is constantly evolving, and so must our approaches to security testing. By implementing the techniques, tools, and best practices outlined in this guide, you’ll be well-equipped to identify vulnerabilities, mitigate risks, and strengthen your software’s defenses.
Remember, effective security testing requires a proactive mindset and continuous learning. Stay informed about emerging threats, regularly update your testing strategies, and foster a security-first culture within your development teams. By doing so, you’ll not only enhance the quality and reliability of your software but also build trust with your users by demonstrating a commitment to protecting their data and privacy.
As quality assurance professionals, we play a pivotal role in ensuring the security of the applications we help develop. Let this tutorial serve as a foundation for your journey in mastering security testing, and may it inspire you to champion security best practices throughout the software development lifecycle.
If you have any queries, please comment below.
Related posts:
- Most popular Security Testing tools
- Penetration Testing – Detailed Guide
- Most popular Penetration Testing tools
- Test Management Tools
- Defect Tracking Tools
- API Testing Tools
- Automation Testing Tools