Penetration Testing Tutorial: How To Perform Penetration Testing
In this penetration testing tutorial (pen test tutorial), we are going to learn the following:

Let’s dive in further to learn Penetration testing without further delay.
What is a Penetration Testing?
Penetration testing is also a type of Security testing which is performed to evaluate the security of the system (hardware, software, networks, or an information system environment). The goal of this testing is to find all the security vulnerabilities that are present in an application by evaluating the security of the system with malicious techniques and to protect the data from hackers and maintain the functionality of the system. It is a type of Non-functional testing that intends to make authorized attempts to violate the security of the system. It is also known as Pen Testing or Pen Test and the tester who does this testing is a penetration tester aka ethical hacker.
Must read: What is PCI Penetration Testing [Step-by-Step Guide]
Why is Penetration Testing necessary?
If a system is not secured, then an attacker can take authorized access to the system. Penetration testing evaluates the security of a system and protects it against internal and external threats. It identifies the vulnerabilities and determines whether unauthorized access or other malicious activity is possible.
Organizations conduct penetration testing for a number of reasons
- To prevent data breaches
- To check security controls
- To meet compliance requirements
- To ensure the security of new applications
- To access incident detection and response effectiveness
How often to conduct pen testing?
Cyber-attacks are quite often in current days. It is very important to conduct regular vulnerability scans and penetration testing to detect recently discovered and previously unknown vulnerabilities.
The frequency of conducting pen testing should depend on your organization’s security policy. However, conducting pen testing regularly can determine the weaknesses of your system and keep it stay away from security breaches.
Usually, pen testing is done after the deployment of new infrastructure and applications. Also, it is done after major changes to infrastructure and applications.
Vulnerability scanning examines the servers for vulnerabilities. We have to make sure the vulnerabilities we found are not false positives. Actually reporting false positives is a downside of vulnerability scanning.
Penetration testing examines the servers for vulnerabilities and exploits them.
Both vulnerability scanning and penetration testing can test an organizations ability to detect security breaches. Organizations need to scan both the external and internal infrastructure and applications to protect against external and internal threats.
Organizations have to conduct regular penetration testing for the following reasons:
- To find security vulnerabilities in a system
- To secure user data
- To test applications that are often the avenues of attack
- To identify new bugs in an existing system after deployment or after major changes done in the system
- To prevent the black hat attacks and guards the user data
- To control revenue loss
- To improve the existing security standards
What are the phases of Penetration Testing?
The process of penetration testing can be divided into five phases, which are as follows:
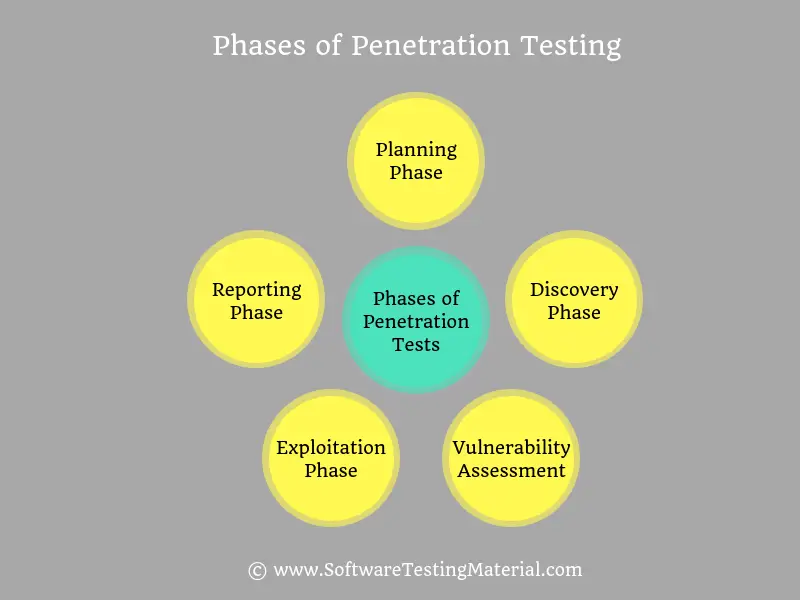
1. Planning Phase
In this phase, we define the scope (which system to test and the goals and objectives to achieve with the penetration test) and the resources and the tools (vulnerability scanners or penetration testing tools) to employ for test execution
2. Discovery Phase
In this phase, we collect as much information as possible about the systems that are in the scope of the penetration test.
3. Vulnerability Assessment Phase
In vulnerability assessment, we just identify and report the vulnerability using vulnerability scanning tools.
4. Exploitation Phase
In this phase, we try to exploit the vulnerabilities identified in the previous phase (i.e., discovery phase) to gain access to the target system.
5. Reporting Phase
In this phase, we document all the results and findings in an effective manner. This report will be used as a reference document while mitigating activities to address the identified vulnerabilities.
What are the root causes of Security Vulnerabilities?
Some of the root causes of Security Vulnerabilities are as follows
- Complexity: Security vulnerabilities rise in proportion to the complexity of a system. Complexity in terms of software, hardware, information, businesses, and processes introduce more security vulnerabilities.
- Connectivity: Every unsecured connection is a potential avenue for exploitation.
- Design Flaws: There shouldn’t be any design bugs in software and hardware. These bugs can expose businesses to significant risks.
- Configuration: Poor system configuration introduces security vulnerabilities.
- User Input: Data received through SQL injections, buffer overflows etc., can be designed to attack the receiving system.
- Management: Management should have a proper risk management plan to avoid security vulnerabilities in the system.
- Passwords: Passwords are there to avoid unauthorized access and secure your personal data. Unsecured passwords (sharing with others, writing them down somewhere, setting easy to guess) allows hackers to guess your password easily.
- Lack of training: Lack of training leads to human errors. Human errors can be prevented by giving proper training to the employees.
- Human errors: Human errors such as improper disposal of documents, coding errors, giving out passwords to phishing sites are a significant source of security vulnerabilities.
- Communication: Communication channels such as telephone, mobile, internet give scope for security vulnerabilities.
- Social: Employees disclosing sensitive information with outsiders is one of the common reasons for security threats.
What is the difference between Penetration Testing & Vulnerability Scanning?
Before looking into the difference between penetration testing and vulnerability scanning. Let’s see two most used terms such as vulnerability and exploit.
What is a Vulnerability?
A vulnerability is a security weakness or flaw which can be exploited by an attacker, to perform unauthorized actions within a system.
What is an Exploit?
An exploit is a software program that takes advantage of a vulnerability to cause unintended behavior to occur on a system. This action is done to gain control of a system to attack it.
Now let’s see the difference between Penetration Testing and Vulnerability Assessment.
There is a confusion in the industry on the difference between Penetration Testing & Vulnerability Scanning. Even though these two terms are commonly interchanged but there are some differences between these two terms. Penetration testing is not the same as the Vulnerability testing.
Vulnerability Scanning
In vulnerability scanning (aka vulnerability assessment), we just identify and report the vulnerability using vulnerability scanning tools.
It’s the first step to improve the security of a system.
A vulnerability assessment report should contain the title, the description and the severity of a vulnerability.
Penetration Testing
In Penetration testing (aka Pen test), we identify the vulnerabilities and attempt to exploit them using penetration testing tools. We repeat the same penetration tests until the system is negative to all those tests.
A penetration testing report lists the vulnerabilities that were exploited successfully.
If an organization is interested in protecting their system from security issues then they should carry out vulnerability assessment and penetration testing on a regular basis.
Pen testing can be divided into three techniques such as manual penetration testing, automated penetration testing and a combination of both manual & automated penetration testing.
By using automated penetration testing tools, it is not possible to find all vulnerabilities. Some vulnerabilities can be identified using a manual scan. So, experienced pen testers use their experience and skills to attack a system using manual penetration testing.
Who Performs Pen-testing?
Pen-testing can be performed by Testers or Network Specialists or Security Consultants.
Role and Responsibilities of Penetration Testers
Responsibilities of penetration testers vary from company to company. However, there are several core responsibilities common to all pen testers such as
- Understand complex computer systems and technical cybersecurity terms
- Collect the required information from the organization to enable penetration tests
- Plan and create penetration methods, scripts, and tests
- Carry out onsite testing of clients infrastructure and remote testing of clients network to expose weaknesses in security
- Work with clients to determine their requirements from the test
- Conducts penetration testing and vulnerability scanning using automated tools, ad-hoc tools, and manual testing
- Ability to analyze root causes and deliver strategic recommendations during security reviews
- Create reports and recommendations from your findings
- Understand how the flaws that you identify could affect business, or business function if they’re not fixed.
- The flaws that you identify should be reproducible so that it will be easy for developers to fix them
- All the data and information should be kept confidential
Types of Penetration Testers?
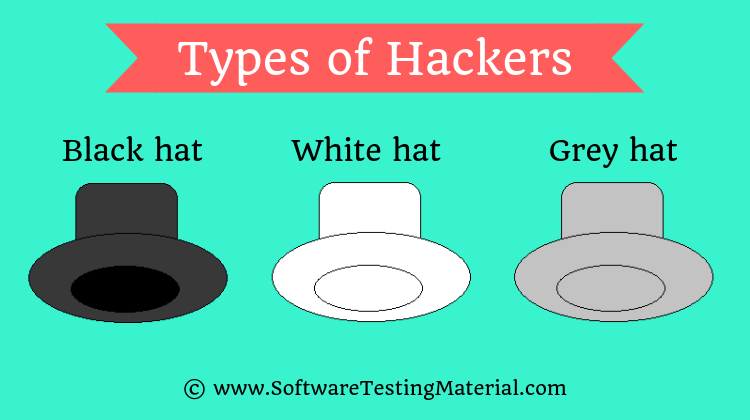
- Black hat penetration testers
- White hat penetration testers
- Grey hat penetration testers
What is the difference between Black, White and Grey hat hackers?
Black Hat Hackers
Black hat hackers (aka Black hats) are considered as cybercriminals. They use their skills with an evil motive for personal or financial gains. They break into computer networks to destroy data or make the system unusable for those who are authorized to use the system. Usually, they involve in hacking banks, stealing credit card information, creating and using a botnet to perform DDoS (Distributed Denial of Service) attacks etc.,
White Hat Hackers
White hat hackers (aka White hats) are usually called ethical hackers. Ethical hackers work for good reasons rather than evil. Usually, companies recruit these white hat hackers as full-time employees and also some companies work with these white hat hackers on contract basis as security specialists to find security loopholes of their system. White hat hackers attack a system after getting permission from the owner of the system.
Grey Hat Hackers
Grey hat hackers (aka Grey hats) may hack a system for ethical and unethical reasons. Activities of these Grey hat hackers fall somewhere between black hat hackers and white hat hackers. Grey hat hackers find vulnerabilities in a system. This type of hacking is considered illegal because they attack the system without getting permission from the owner of the system. They find for the security vulnerabilities but not for bad purposes. After finding security vulnerabilities, they report them to the owner of the system. Sometimes they request a fee to fix the issue. If the owner doesn’t respond then sometimes the hackers will disclose the security flaw to the public.
What are the types of Penetration Tests?
Different types of Pen Testing which are as follows
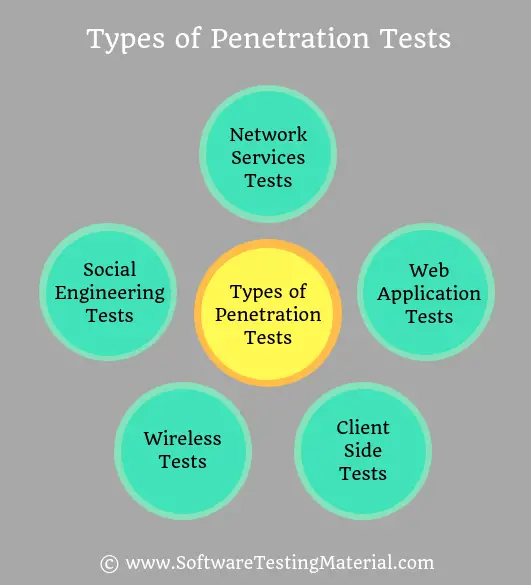
#1. Network Services Tests
Network services pen test aims to identify security weaknesses and vulnerabilities in the network. These tests can be run both locally and remotely.
Pen testers should target the following network areas
- Firewall config test
- Stateful analysis test
- Firewall bypass test
- IPS deception
- DNS level attacks such as Zone transfer testing, Switching or routing issues, and another required network testing
Pen testers also cover some of the most common software packages such as
- Secure Shell (SSH)
- SQL Server or MySQL
- Simple Mail Transfer Protocol (SMTP)
- File Transfer Protocol (FTP)
#2. Web Application Tests
Web application pen tests (web application penetration testing) aim to identify the security vulnerabilities of web applications, web browsers, and their components like ActiveX, Applets, Silverlight and APIs.
#3. Client Side Tests
Client-side pen tests aim to find security vulnerabilities and exploit them in client-side software applications.
#4. Wireless Tests
Wireless pen tests are involved in analyzing the Wi-Fi networks and wireless devices deployed on the client site. Wireless devices such as laptops, netbooks, tablets, smartphones, iPods etc.,
#5. Social Engineering Tests
Employees disclosing sensitive information with outsiders is one of the common reasons of security threats. All the employees should follow security standards and policies to avoid social engineering penetration attempt. These tests are mostly done through communication channels such as telephone, mobile, internet and it targets employees, helpdesks and processes.
Social engineering pen tests can be subcategorized into two types
#1. Remote Tests
Remote tests intend to trick an employee to disclose sensitive information via an electronic means (ie., via Phishing Email Campaign)
#2. Physical Tests
Strong physical security methods should be applied to protect sensitive information. It involves human handling tactics like convincing an employee via phone calls. It is generally using in a military facility.
What are the Types of Pen Testing?
There are three types of Pen Testing which can be used, which are as follows
1. Black Box Penetration Testing
2. White Box Penetration Testing
3. Grey Box Penetration Testing
#1. Black Box Penetration Testing
In Black Box Penetration Testing approach, black box pen testers (Black Hat Hackers) assess the target system without having any knowledge of system details. They just have high-level details about the system such as URL or company name. They don’t examine any programming code. These testers are not ethical hackers. It’s impossible to gather information about the target system from the owner of the system. So they launch an all-out, brute force attack against the system to find out weaknesses or vulnerabilities in a system. This approach is also referred as “trial and error” approach.
#2. White Box Penetration Testing
In White Box Penetration Testing approach, white box pen testers (White Hat Hackers) access the target system with complete details about the system. Since they have complete details about the system, white box test can be accomplished much quicker compared to black box test. White box pen testers are called ethical hackers. This approach is also known as clear box, glass box, open box and structural testing.
#3. Grey Box Penetration Testing
In Grey Box Penetration Testing approach, grey box pen testers (Grey Hat Hackers) utilize both manual and automated testing processes. It is a combination of both Black Box and White Box penetration testing techniques. These hackers may attack a system for ethical and unethical reasons. These hackers find vulnerabilities in a system. This type of hacking is considered illegal because they attack the system without getting permission from the owner of the system.
Limitations of Penetration Testing
Penetration testing cannot find all vulnerabilities in a target system. There are some limitations based on the resources and restrictions of a test, such as
- Limitations of skills of a pen tester – It’s hard to find professional pen testes.
- Limitations of scope – most of the organizations leave some tests due to a resource, security constraints etc.,
- Limitations of time
- Limitations of budget
- Limitations of tools used
How to choose Penetration Testing Tools?
We need to choose a penetration testing based on the following points.
- It should be easy to use
- It should be easy to configure & deploy
- It should scan vulnerabilities easily
- Categorization of vulnerabilities based on the severity
- It should generate detailed reports and logs
- It should be cost-effective in terms of budget
- A good support team & technical documentation is essential
Top Penetration Testing Tools
Pen Testing Tools are classified into Vulnerability Scanners and Vulnerability Attackers. Vulnerability Scanners show you the weak spots of the system whereas Vulnerability Attackers show you the weak spots of the system and attack them.
Some of the popular Penetration Testing Tools are as follows
#1. Invicti

Invicti is a web application security scanner. This web application security scanner is easy to use and the results will be deadly accurate. It is used to automatically identify security issues such as SQL injection and Cross-Site Scripting (XSS) in websites, web applications, and web services. Its Proof-based Scanning technology doesn’t just report vulnerabilities, it also produces a Proof of Concept to confirm they are not false positives.
Some of the features of Invicti are as follows
- Vulnerability assessment
- Advanced web scanning
- Proof-based scanning technology for dead-accurate vulnerability detection and scan results
- Full HTML5 support
- Web services scanning
- HTTP request builder
- SDLC integration
- Reporting
- Exploitation
- Manual testing
- Anti-CSRF (Cross-site Request Forgery) token support
- Automatic detection of custom 404 error pages
- REST API support
- Anti-CSRF token support
#2. Acunetix

Acunetix is a web vulnerability scanner that automatically scans any website. It detects over 4500 web vulnerabilities which include all variants of SQL injection, XSS, and Host Header Injection. Users can export the vulnerabilities to issue trackers such as Atlassian JIRA, Bugzilla, GitHub, GitLab etc.,
Don’t miss our detailed review on Acunetix
Some of the features of Acunetix are as follows
- In-depth crawl and analysis – automatically scans all websites
- The highest detection rate of vulnerabilities with low false positives
- Integrated vulnerability management – prioritize and control threats
- Integration with popular WAFs and issue trackers such as JIRA, GitHub, TFS
- Free network security scanning and Manual Testing tools
- It supports Windows, Linux, and macOS
Check our detailed review and comparison guide on the best Penetration Testing Tools for more details.
What are some of the free Penetration Testing Tools?
Some of the free penetration testing tools (network vulnerability assessment tools/web vulnerability assessment tools) are NMap, Nessus, Metasploit, Wireshark, OpenSSL, W3af, etc.,
What are some of the commercial Penetration Testing Tools?
Some of the commercial penetration testing tools are Invicti, Acunetix.
Conclusion
We’ve prepared this tutorial by keeping software testers in mind and covered everything needed for them to learn and implement Penetration Testing at work. Even though it’s a beginner’s guide for Penetration Testing, we hope you would be able to improve your knowledge on Penetration Testing with this tutorial.
If you have any queries, please comment below. If you are a penetration tester, please share your experience in the comment section below.
Related posts:
- Best Dynamic Application Security Testing (DAST) Software
- Best Vulnerability Assessment Scanning Tools
- Best Penetration Testing Companies
- Best Nessus Alternatives
- Best Burp Suite Alternatives
- Best Penetration Testing Tools
- Penetration Testing Guide
- Best Security Testing Tools
- Best Web Application Testing Tools
- Security Testing – Detailed Guide