What is SCP (Secure Copy Protocol)
In the tech world today, secure data transfer is a big deal. That’s where SCP, or Secure Copy Protocol, comes in. This article is going to break down everything you need to know about SCP.
We’ll go over what it does, how it works, and why it’s crucial for digital communication. Ready to deep dive into the world of Secure Copy Protocol? Let’s get started.
What is SCP?
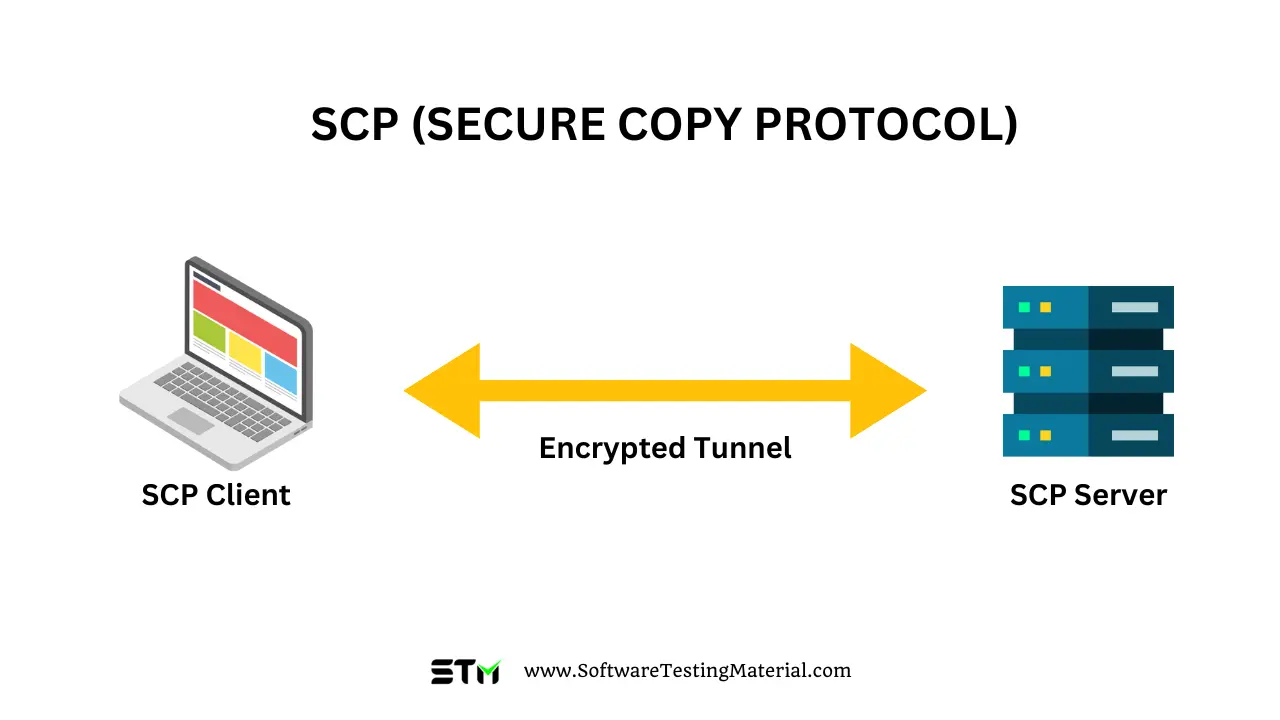
SCP, also known as Secure Copy Protocol, is a network protocol designed for secure file transfer between a local host and a remote host, or between two remote hosts.
It combines the functionality of the Remote Copy Protocol (RCP) for file transfer and the Secure Shell (SSH) protocol for encryption and authentication.
One of the key advantages of SCP is its ability to preserve access permissions and timestamps of files during the transfer process.
This makes it an ideal choice for transferring data when these attributes are crucial.
With its emphasis on security and integrity, SCP provides a reliable option for administrators and users who need to transfer sensitive data across networks.
How the SCP protocol works
Secure Copy Protocol (SCP) is a method of securely transferring computer files between a local and a remote host or between two remote hosts. It’s based on the Secure Shell (SSH) protocol, which provides the encryption for the transfer. Here’s a simple breakdown of how it works:
- The SCP command initiates a connection to the remote host. This is done by providing the host name, username, and the location of the files to be transferred.
- The remote host, upon receiving the connection request, authenticates the user. This is typically done through a password, but other SSH-based authentication methods like public key authentication are also used.
- Once authenticated, a secure connection is established between the local and remote host. This is the SSH tunnel, which provides the secure path for the file transfer.
- The files are then transferred along the SSH tunnel from the source to the destination. The transferred data remains encrypted until it reaches the destination.
- After the transfer is completed, the connection is closed.
In essence, SCP is all about establishing a secure connection and then using that connection to transfer files. Its reliance on SSH for the underlying security makes it a robust and secure option for file transfers.
What is the SSH File Transfer Protocol?
The SSH File Transfer Protocol, also known as SFTP, is a network protocol that provides file access, file transfer, and file management functionalities over secure channels.
Designed as an extension of the Secure Shell protocol (SSH) to provide secure file transfer capabilities, SFTP is the standard for secure file transfer operations among servers on the internet.
It encrypts both commands and data, preventing passwords and sensitive information from being transmitted in the clear over the network.
It is functionally similar to FTP, but because it uses a different protocol, you can’t use a standard FTP client to talk to an SFTP server, nor can you connect to an FTP server with a client that supports only SFTP.
What is the relationship between SCP and SSH?
The Secure Copy Protocol (SCP) is a technology that stems from the Secure Shell (SSH) protocol.
SCP leverages the underlying infrastructure of SSH to enable secure and authenticated file transfers.
In essence, SCP and SSH share a closely intertwined relationship, with SCP essentially acting as an extension of SSH.
This relationship allows SCP to offer reliable, secure file transfers, effectively preventing unauthorized access and ensuring data integrity during the transmission process.
Notably, while SSH provides a secure channel for executing commands on a remote server, SCP extends this functionality by allowing the secure transfer of files between hosts.
SCP vs SFTP
| Factor | SCP | SFTP |
|---|---|---|
| Protocol | SCP is a simple protocol supporting only file transfers. | SFTP is a more robust protocol, supporting a range of operations such as file transfer, file access, and file management. |
| Error Reporting | SCP does not support comprehensive error reporting mechanisms, which means that failed transfers may not be adequately reported. | SFTP supports detailed error reporting, which can be crucial in diagnosing transfer-related issues. |
| Resuming Transfers | SCP does not inherently support the resumption of interrupted transfers. | SFTP supports the resumption of file transfers, allowing incomplete downloads/uploads to be continued from where they left off. |
| Directory Listings | SCP does not support remote directory listings. | SFTP supports remote directory listings, enhancing file navigation operations. |
| Speed | SCP is generally much faster in transferring files, especially on high-latency networks. It doesn’t have to wait for packet acknowledgment unlike SFTP. | SFTP is slower than SCP this is because SFTP has to acknowledge every tiny packet. |
| Security | SCP relies on the SSH protocol for security, providing a safe and efficient data transfer. SCP leverages SSH for providing features like password and data-in-motion encryption, and public-key authentication, ensuring high data transfer security. | SFTP also utilizes SSH for secure transfers. However, unlike SCP, it also allows for the use of public key authentication. SFTP leverages SSH for providing features like password and data-in-motion encryption, and public-key authentication, ensuring high data transfer security. |
| Large file transfer support | There are no file size limitations | There are no file size limitations |
Conclusion
The Secure Copy Protocol (SCP) serves as a reliable courier, facilitating the secure and efficient transfer of our crucial data – be it images, documents, or multimedia files – from one node to another.
As we entrust a mail carrier with the confidential delivery of our physical mail, so we rely on SCP to protect our digital assets from prying eyes during transit.
In the fast-evolving world of online data sharing, it’s crucial to prioritize security protocols like SCP. They play a vital role in safeguarding your information.
In essence, SCP functions as an unseen guardian, continuously operating in the backdrop to ensure the smooth and secure functioning of our digital interactions.
Related posts:
- What is an FTP (File Transfer Protocol)
- What is FTPS Server (File Transfer Protocol Secure)
- What is SFTP Server (Secure File Transfer Protocol)
- What is MFT (Managed File Transfer)
- 14 Popular File Transfer Protocols For Business Explained
- What is AS2 (Applicability Statement 2)
- MFT Vs SSH: Whats the difference
- Difference between MFT vs SFTP