Leverage RPA Testing For Better Anomaly Detection

How To Leverage RPA Testing For Better Anomaly Detection?
In the world of Software testing and testing automation, a new revolution has been quite popular and is the buzz of many enterprises and businesses these days. This revolutionary technology is popularly known as RPA – Robotic Process Automation.
Softwares developed around the world needs constant testing for performance and security needs. Cybersecurity has always seen anomalies as a formidable enemy. While RPA does help in automating the software testing, can it help secure the softwares too?
Let us begin with what we need RPA to help with?
Anomaly Detection: What is an Anomaly and how it is detected?
Anomalies are patterns in any data set that behaves differently than the normal. As you can see in the below figure, most of the data sets are in N1 and N2 regions and the data sets other than these two regions or far away from these regions will be deemed as Anomalies.
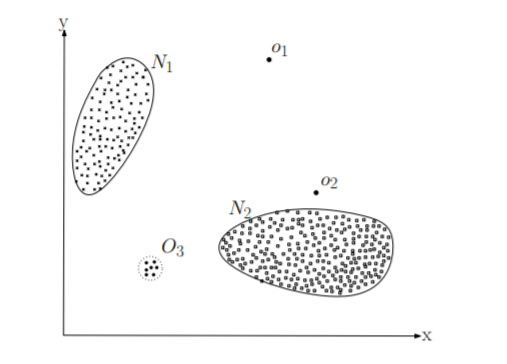
The most important challenge in Anomaly detection in data sets of software is to differentiate between the novel patterns and Anomalies or malicious data sets that can harm the software or leak important information.
These Anomalies are mostly used for malicious attacks, cyber frauds, identity thefts, and data leaks. Thus, detection of Anomalies is vital to your software’s continuous testing to avoid any incident.
Ways of Detection that exist:
IDS:
An Intrusion Detection System is a software tool used for the detection of unauthorized access to a network or system. It is capable of detecting all types of malicious usage of a computer or a network. This detection also includes vulnerable service attacks, data-driven attacks on software and applications.
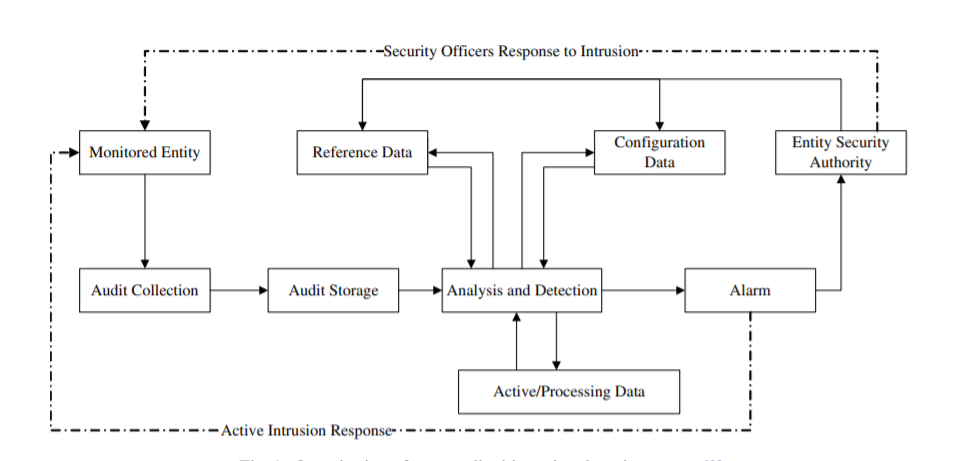
An IDS can be considered a “network sniffer”, as it collects all the network packets and analyzes them through an algorithm to look for any rule violations predefined by the network infrastructure, once the violations are detected, anomaly pattern detection becomes relatively easy.
Statistical Anomaly Detection:
This anomaly detection method is purely based on the data sets. The system analyzes a subject or software for example and creates a profile of each function and activity of the software users and background activities.
Further, these profiles include measure of activities and its intensity, audit record distribution measure and match the activity profiles with the novel activity patterns to detect the anomalies in the patterns.
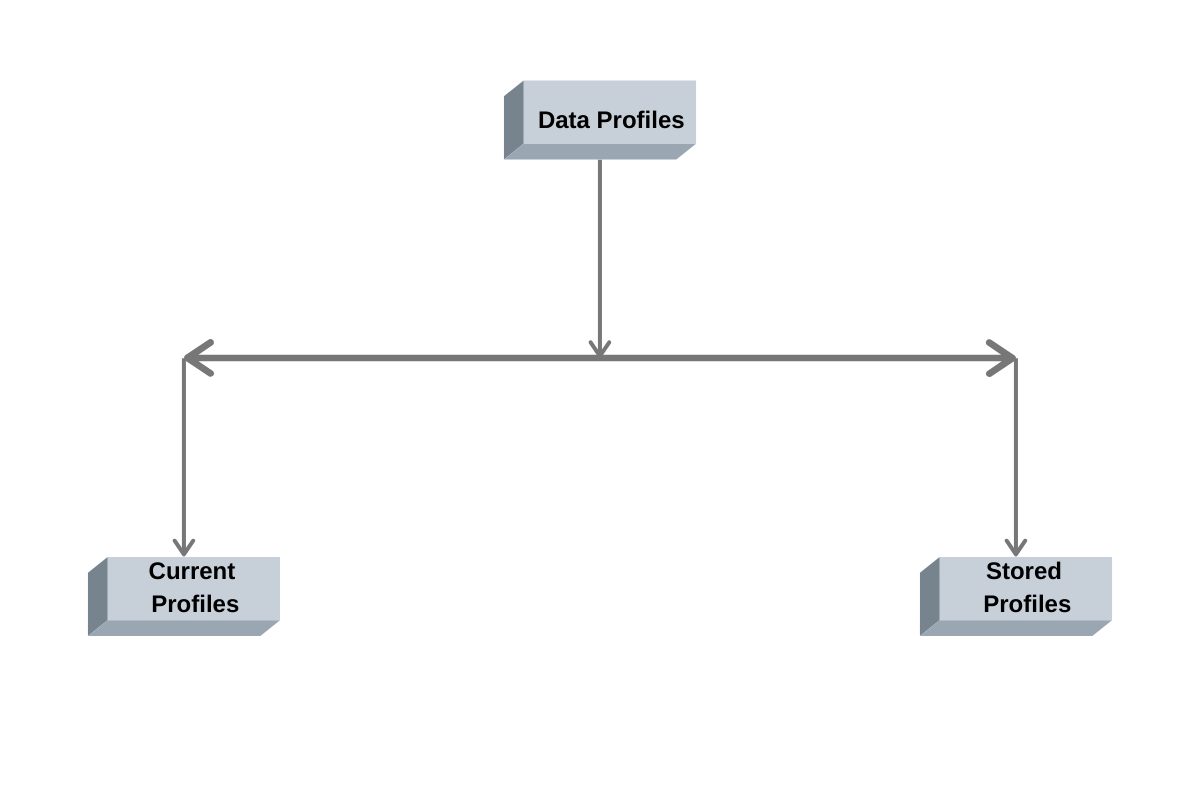
There are two basic profiles generated: Current profile and Stored profile. As the events of the system -in our case, software or a network occur, a current profile is created that can be matched with the stored profile and the IDS can be used for the detection of different patterns.
Signature Technique:
A detection technique that is based on identifying the different signatures or attack patterns other than the predefined patterns already redefined. By targeting specific patterns and signatures, the system matches the incoming patterns or packets of data with known attack signatures.
Haystack:
An IDS technique that reports the Anomalous data in the audit trail files by the end of the day. It also analyzes all the user activities and behavior and matches it with the predefined metrics for anomaly patterns.
Several other techniques that are used for Anomaly detection including Machine Learning techniques that employ different algorithms like Isolation Forest, Histogram-based outlier detection, Cluster-based outlier detection, etc.
Now, let us discuss what is RPA and how can we use the same for better Anomaly detection.
What is RPA?
This is a revolutionary technology of using robots to reduce human intervention and increase the automation of business processes. This technology does not replace humans with robots, but, it has automated softwares and programs run on the end-users devices that automate the process based on predefined business strategies or metrics.
On the basic principle, RPA can be applied to any business operation. Coming back to our realm! Our take is on usage of RPA for Anomaly detection during the testing of softwares.
So, let us first discover how RPA helps in software testing?
Software testing is a very broad term and includes several testing levels like unit testing, integration testing, system testing, and acceptance testing. All of these levels needs integration of the RPA infrastructure and processes.
Software Testing RPA:
RPA provides automation and we can automate the software testing process through RPA. This can surely help in minimizing the testing team efforts and errors that can occur during the testing process
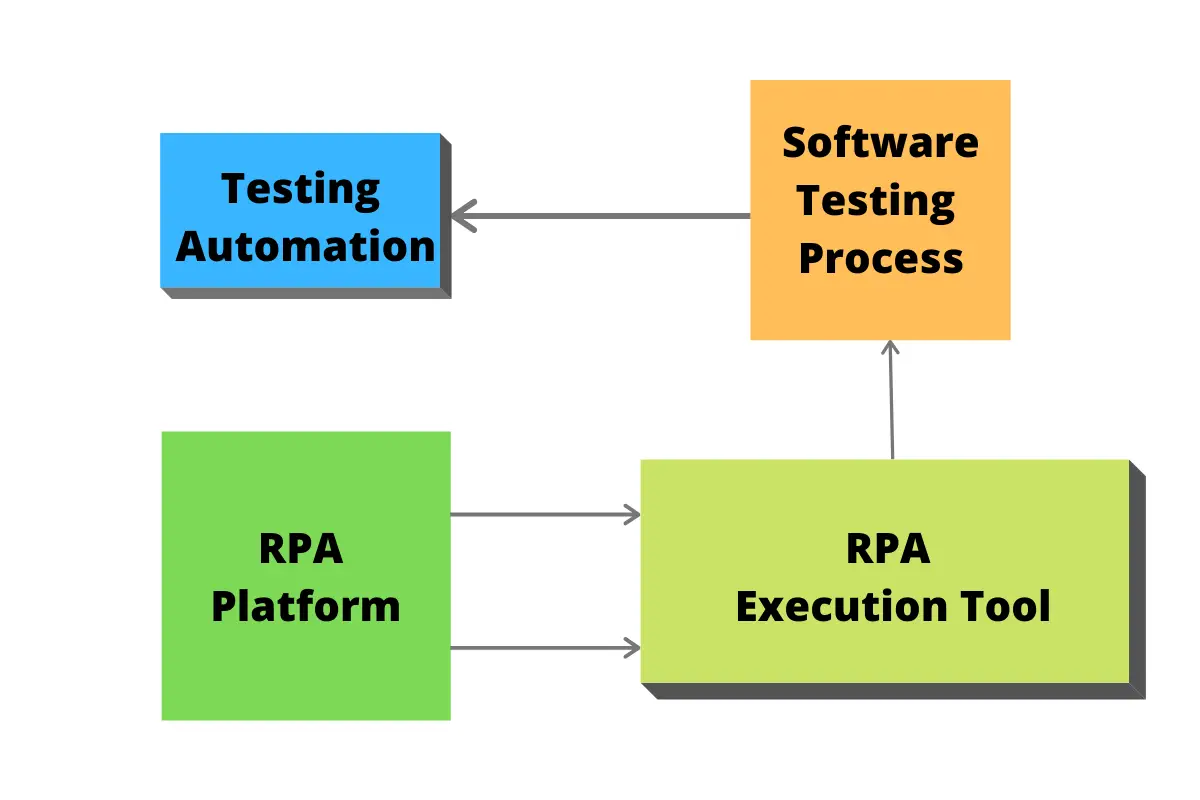
Software testing in RPA-based system requires four basic components:
RPA Platform:
These are formed of repositories that store all the required codes and programming of an RPA software bot. These are kept as shared repositories for accessibility. RPA platform provides all the support that RPA software bot and RPA tools require to automate a testing process.
RPA Tools:
RPA tools are the builders of an automated process. It uses the data of RPA software bots stored in the repositories for the creation of software bots for testing purposes. It also helps with exception handling, form data sources and builds reusable components for software testing and version integration.
Here is the list of RPA Tools
Configuration of Software Testing Process:
The software testing process is configured through the RPA Tool that builds the RPA software bots. These bots configure all the necessary metrics for testing and help integrate those parameters while the execution of tests takes place automatically without human intervention.
Testing Automation:
Testing automation is achieved by automatic detection of errors and the creation of testing scenarios through RPA tools. RPA software bots analyze all the testing data recorded during these testing scenarios and detect any erroneous process, feature or even code that could hamper the overall performance of the software by matching the results with configured metrics.
RPA for Anomaly detection:
As we saw earlier the RPA tool helps configure the metrics of testing scenarios and software performance, the same can be used for capturing the data profiles or signature of attacks to match it with the stored profile or already known attack signatures.
RPA software robots can match these profiles or signatures automatically and detect any malicious patterns or Anomaly signature. Thus, RPA software bots can successfully automate the Anomaly detection and help with better detection of the malicious patterns that can disrupt the performance of the software.
Signing Off:
With more companies switching to mobile app development and software development, testing of apps and software have become a continuous process. To cope up with this continuous process, software testing providers and organizations are now using RPA tools to automate testing processes.
With RPA based Anomaly detection, the security of the software testing process takes centerstage and along with the continuous testing of software, the secure operations of software for longer periods can be ensured.
Author Bio
Manoj Rupareliya is a Marketing Manager at AppEmporio – Mobile App Development Company. who has been writing for various blogs. He has previously covered an extensive range of topics in his posts, including Business, Technology, Finance, Make Money, Cryptocurrency, and Start-ups.