Device Control Software
Lockdown, Control & Monitor USB and peripheral ports
- #1 Cross-Platform coverage; including macOS, Windows, and Linux
- Granular management on all data movement
- Ideal for both Small Businesses and Enterprises
Award-winning enterprise DLP, recognized as a premier solution in Gartner's Enterprise DLP Magic Quadrant
See all awards & certifications



"Excellent support and product. Would recommend to colleagues who require a strong DLP solution."
Jun 28, 2022 - G2 Reviews
Nicholas K.
IT Security and Network Specialist
Enterprise (>1000 employees)
"Great tool for enterprises"
Oct 04, 2022 - G2 Reviews
Verified Endpoint Protector user
Information Technology and Services
Enterprise (>1000 employees)
"Endpoint Protector fills a gap for most companies."
Jun 28, 2022 - G2 Reviews
Verified Endpoint Protector user
Defense & Aerospace
Mid-Market (51-1000 employees)
"Works perfectly for our organization"
Aug 04, 2023 - G2 Reviews
Verified Endpoint Protector user
IT Services
Enterprise (>1000 employees)
Trusted by
Lockdown, control, and monitor USB and peripheral ports to stop data theft and data loss

Auto Detect New Devices
The Device Control software automatically scans, identifies, and classifies new connected external devices used by employees.

Reliability & Privacy
Resistant to connectivity drops and geographical restrictions to give you the highest level of performance and privacy possible.

Grows with you
Easily expandable to include complete data loss prevention capabilities at the endpoint with Content Aware Protection.
Four layers of data protection
Device Control
USB & Peripheral port control
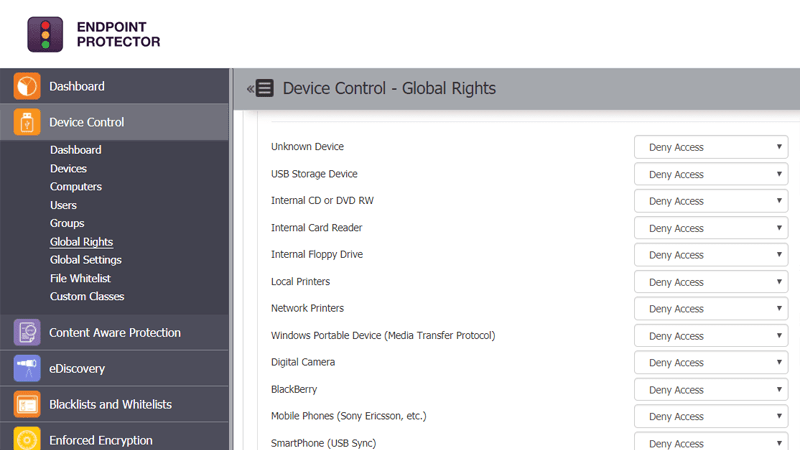
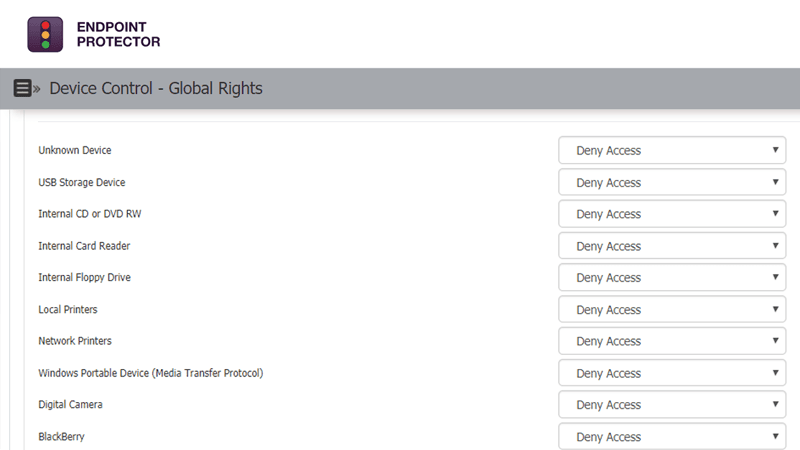
Define granular access rights for removable devices and peripheral ports and establish policies for users, computers and groups, maintaining productivity while enforcing device security.
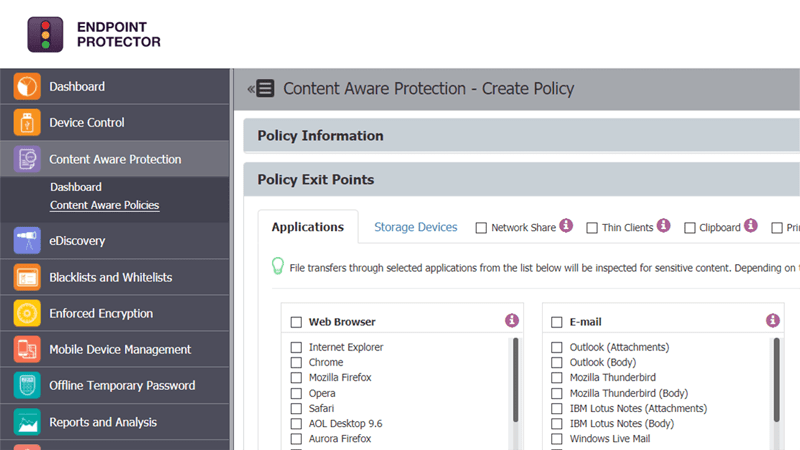
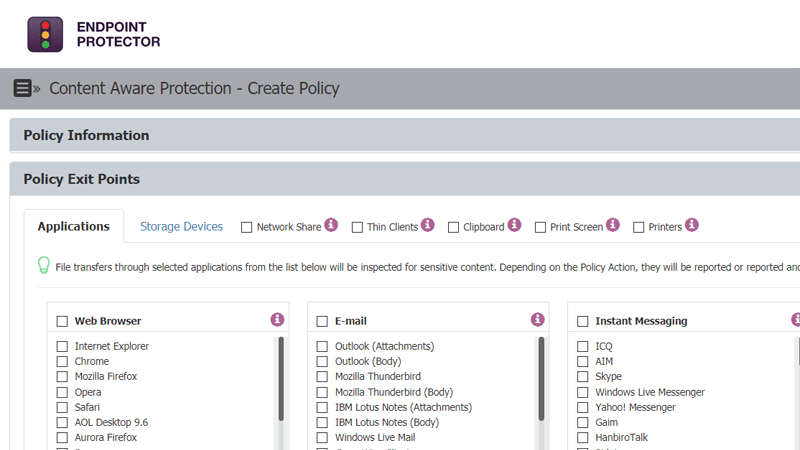
Content-Aware Protection
Scanning data in motion
Prevent data leakage through all possible exit points, from clipboard, screen captures, USB devices, to applications including Microsoft Outlook, Skype or Dropbox.
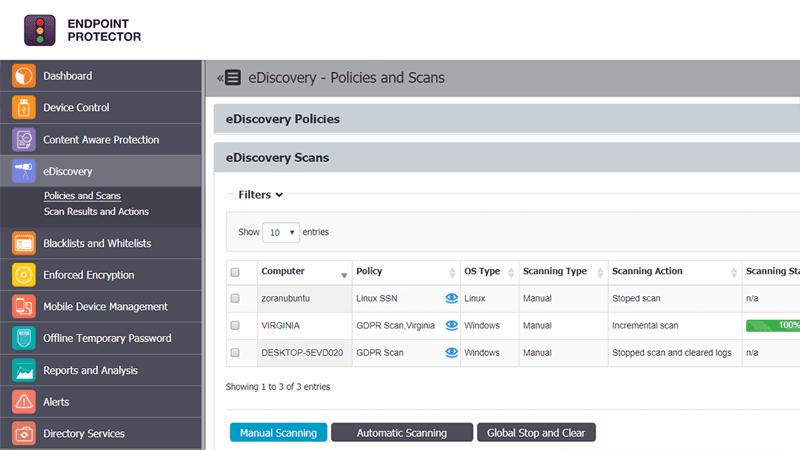
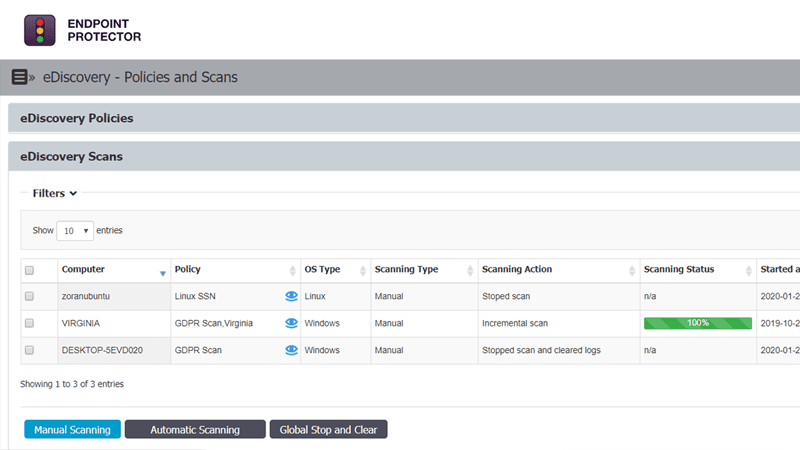
eDiscovery
Scanning data at rest
Prevent data breaches by scanning and identifying sensitive data at the endpoint level on Windows, macOS, and Linux computers. Ensure compliance with regulations like HIPAA, PCI DSS and others.
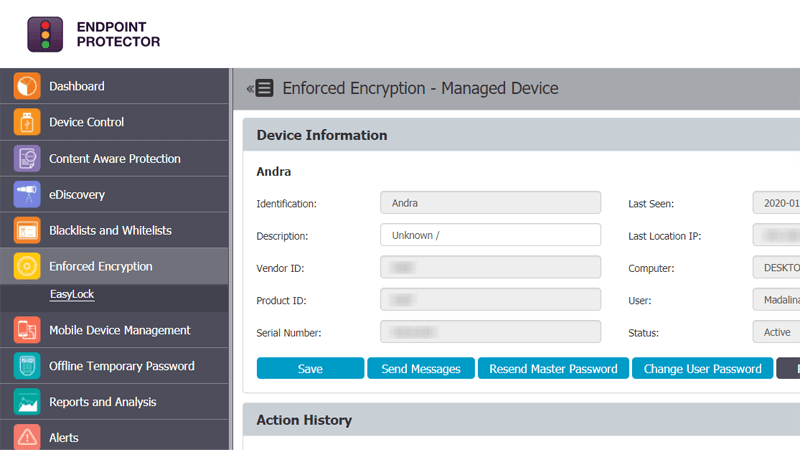
Enforced Encryption
Automatic USB encryption
Encrypt, manage and secure USB storage devices by safeguarding data in transit. Password-based, easy to use and very efficient.
Gain full control of USB devices, Bluetooth and peripheral ports
The centrally-managed Device Control module allows for granular control over USB device permissions, enabling full control of the USB ports and connected storage devices. This way, it prevents accidental or intentional data loss and data leaks, while also protecting the endpoints against the spread of USB malware, BadUSB attacks or viruses. With this module, businesses can centralize user access management and customize access permissions for removable device media connections.


How Device Control works
Device Control module is the first layer of security provided by Endpoint Protector. By defining granular access rights for removable storage and peripheral ports, device security is enforced while productivity, functionality, and workflow is maintained. As a cross-platform solution, it protects the entire fleet of endpoints, regardless of the operating system: Windows, macOS, or Linux.
Controlled device types
Device Control allows easy management for the majority of known USB drive types, for enhanced data protection in various work environments.
- USB Storage Devices (USB Flash Drives, Sticks, Pen drives, etc.)
- External HDDs (incl. sATA HDDs)
- CD/DVD-Players and Burners (internal and external)
- iPhones, iPads and iPods
- Smartphones and Tablets (incl. Android devices, Blackberry and PDAs)
- Digital Cameras
- MP3 Player and other Media Player Devices
- Card Readers (internal and external)
- Memory Cards (SD, MMC, CF, Smartcard, etc.)
- Printers
- Floppy Drives
- Webcams
- WiFi Network Cards
- FireWire Devices
- Biometric Devices
- Bluetooth Devices
- ZIP Drives
- ExpressCard SSD
- Wireless USB
- Serial Port
- Teensy Board
- PCMCIA Storage Devices
- Thunderbolt
- Network Share
- Thin Client Storage (RDP Storage)
- Additional Keyboards
- USB Modems
- Infrared Dongle
Protect company IP, PII, financial data, or other regulated data types without compromising productivity

Intellectual Property (IP) Protection
Endpoint Protector uses advanced technologies such as N-gram-based text categorization to accurately discover IP, including source code, within hundreds of file formats, and then monitor and control any transfers to prevent data theft.

Personally Identifiable Information (PII) Protection
Discover and protect Personally Identifiable Information (PII) and sensitive information stored on employee endpoints with our data discovery module. Monitor data and prevent data exfiltration and data leaks with an all-in-one Data Loss Prevention tool.

Insider Threat Protection
Stop data leakage and data theft and by applying appropriate cybersecurity controls at the endpoint - from logging potential insider threats, to real-time blocking. Discover end-users that fail to follow data security policies and situations that can lead to a policy violation or data leakage.

Compliance and Regulations
Endpoint Protector’s DLP software can help organizations ensure data privacy and achieve regulatory compliance with HIPAA, PCI-DSS, NIST, GDPR, SOX, and others, avoiding fines and other damages imposed by regulatory entities.